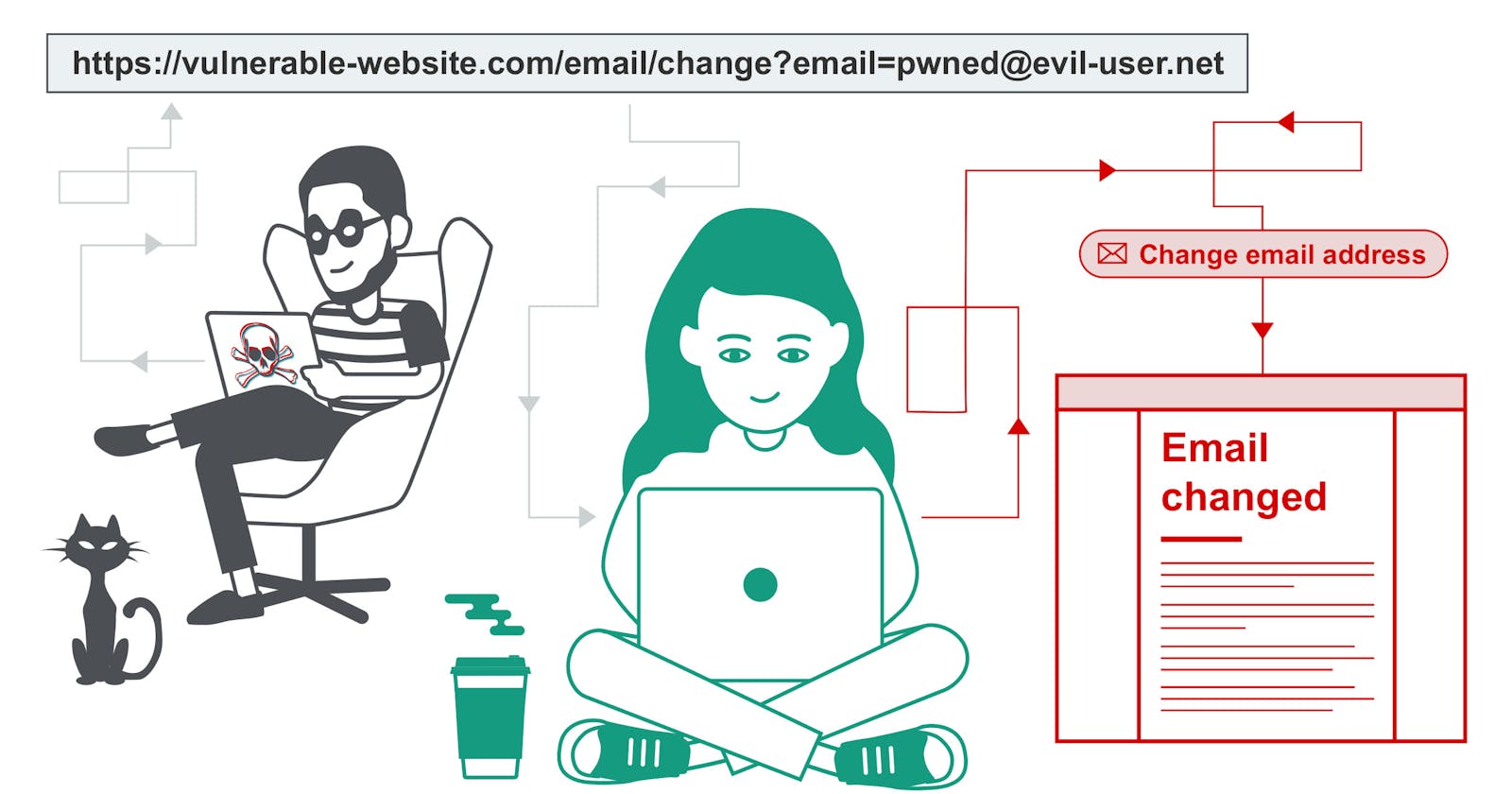
In the ever-evolving landscape of cybersecurity threats, Cross-Site Request Forgery (CSRF) stands out as a formidable adversary. This insidious attack vector takes advantage of three critical conditions to infiltrate web applications and compromise user data. In this tech blog, we delve into the intricacies of CSRF attacks, dissecting the key elements that make them possible.
1. A Relevant Action: Unveiling the Motive
At the core of a CSRF attack lies the existence of a relevant action within the target application. This action catalyzes the attacker's motives, often involving privileged operations or manipulations of user-specific data. For instance, modifying permissions for other users or changing one's password could be the sought-after actions. Understanding these motives is crucial in comprehending the potential impact of CSRF attacks.
2. Cookie-Based Session Handling: The Achilles' Heel
The second condition that paves the way for CSRF exploits is the reliance on cookie-based session handling. Web applications often use session cookies to identify users and validate their requests. In the absence of additional security measures, such as anti-CSRF tokens, attackers can manipulate this reliance on cookies to forge requests on behalf of unsuspecting users. This vulnerability underscores the importance of implementing robust session management practices to thwart CSRF attacks.
3. No Unpredictable Request Parameters: Peering into the Parameters
For a CSRF attack to succeed, the requests triggering the relevant action must not contain unpredictable parameters. In simpler terms, the attacker must be able to determine or guess the values of all parameters involved in the malicious request. For example, if the goal is to change a user's password, the attack is rendered ineffective if the attacker needs knowledge of the existing password. Examining the predictability of request parameters becomes a critical step in fortifying applications against CSRF vulnerabilities.
Conclusion: Fortifying Defenses Against CSRF
In conclusion, understanding the trifecta of conditions that facilitate CSRF attacks is paramount for building robust cybersecurity defenses. Developers and security professionals must remain vigilant in identifying and mitigating vulnerabilities associated with relevant actions, cookie-based session handling, and predictable request parameters. Implementing measures such as anti-CSRF tokens, secure session management, and input validation can fortify applications against the pervasive threat of CSRF attacks.
Stay tuned for our upcoming posts, where we'll explore proactive strategies and best practices to safeguard web applications from CSRF exploits. As the digital landscape continues to evolve, staying ahead of emerging threats is key to ensuring a secure online environment.